7. Asset management#
Asset management is available to all Risk Flow users. Client users have access only to the groups and assets registered for them. Managers and administrators can see all asset groups and their assets and can simultaneously edit them. Users with an analyst or auditor role have read only access to all groups and their assets.
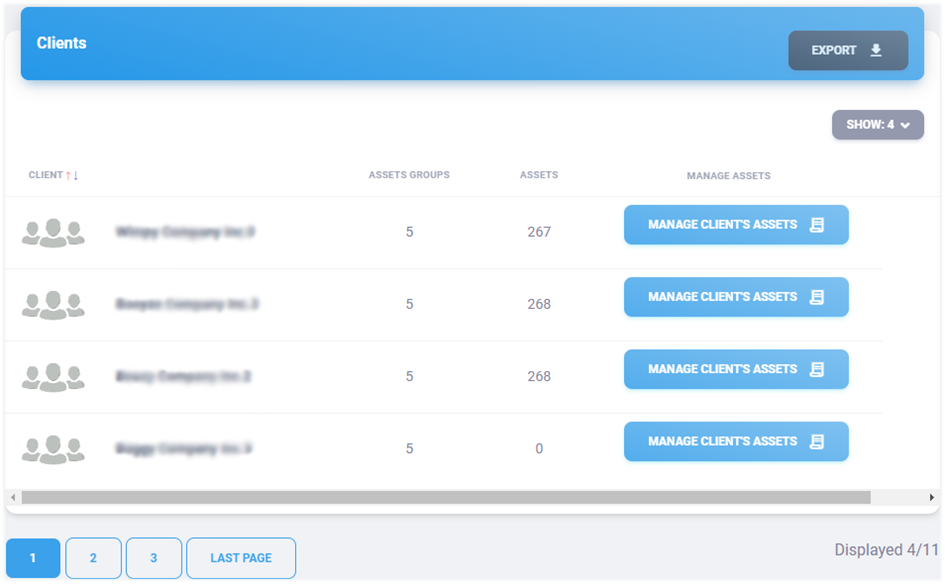
7.1. Clients#
For users with the role of administrator, manager, analyst or auditor, a list of registered clients is displayed when you open asset management. In this list, you can find the total number of asset groups and the total number of recorded assets.
Export to MS Excel#
Export the following values to a Microsoft Excel workbook. The language of the report is adapted by the currently used language of the application.
Column name |
Description |
|---|---|
# |
Record number in the export |
Client |
Client’s name |
Assets groups |
Total number of asset groups |
Assets |
Total number of assets |
Created at |
Date the record was created. |
Creation time |
Time the record was created. |
Created by |
Email of user who created the record. |
Modified |
The date when record was last modified. |
Modification time |
The time when record was last modified. |
Modified by |
Email of user who made the last changes. |
Export to PDF#
The export to PDF format contains an inventory similar to the listing in the application. It contains the following information. The language of the report is adapted by the currently used language of the application.
Column name |
Description |
|---|---|
# |
Record number in the export |
Client |
Client’s name |
Assets groups |
Total number of asset groups |
Assets |
Total number of assets |
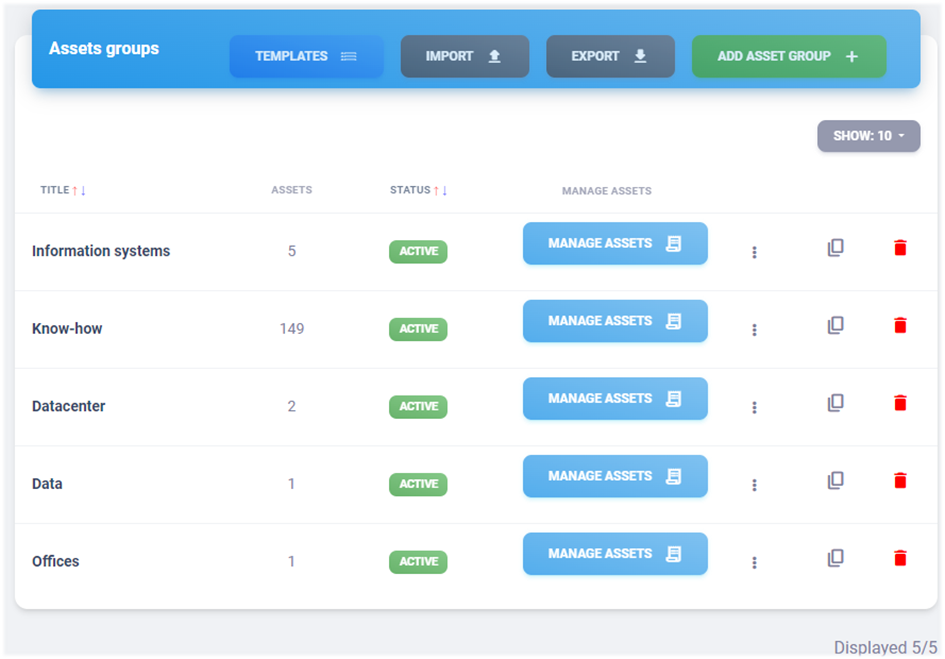
7.2. Asset groups#
After selecting a specific client, a list of its asset groups is
displayed. For users with the role client's user this inventory
will be displayed directly when accessing asset management. The list
contains information about the name of the group, which must be unique
within the client. There is also information about the number of
assets entered and whether the group is active. Only assets from
active groups can be used in risk analyses.
Adding asset group#
The form for adding an asset group can be found at https://INSTANCE-NAME.riskflow.cz/risks/assets/clients/ or after clicking on the “Add asset group” button.
Parameter |
Required |
Description |
|---|---|---|
Group name |
Yes |
Name of the asset group. It must be unique withing the client. |
Active |
No |
An asset group can only be used in the analysis if it is activated. |
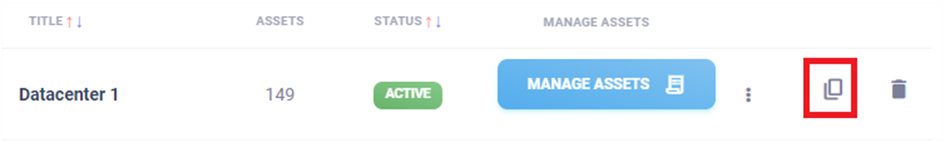
Creating a copy of an asset group#
An authorised user can create copies of asset groups via the copy icon shown in the image below. During the copying process, copies are also created in the asset group of record.
Editing and asset group#
Editing an asset group is possible after opening the edit form by
clicking the three dots icon.
Asset group activation and deactivation#
Activation and deactivation is possible after opening the activation/deactivation form by clicking on the button in the status column. This button can be green or grey and also indicates the status of a particular asset group. Only assets from active groups can be further used for risk analysis.
Deleting an asset group#
You can delete asset groups by clicking on the trash can icon.
When deleting, it is necessary to confirm the action in the modal
window displayed afterwards. Only groups with no assets used in risk
analyses can be deleted.
Export of asset groups#
Export of asset groups is possible in the asset management by clicking
on the Export button and then selecting the export type.
Export to MS Excel#
Exporting asset groups of a specific client to a Microsoft Excel workbook has the following values. The report language is adapted by the currently used application language.
Column name |
Description |
|---|---|
# |
Record number in the export |
Title |
Asset group name |
Assets |
Number of assets in the group |
Status |
Active / Inactive |
Created at |
Date the record was created. |
Creation time |
Time the record was created. |
Created by |
Email of user who created the record. |
Modified |
The date record was last modified. |
Modification time |
The time record was last modified. |
Modified by |
Email of user who made last changes. |
Export to PDF#
Exporting asset groups of a selected client to PDF format contains a list of asset groups similar to the listing in the application. It contains the following information. The language of the report is adapted by the currently used language of the application.
Column name |
Description |
|---|---|
# |
Record number in the export |
Title |
Asset group name |
Assets |
Number of assets in the group |
Status |
Active / Inactive |
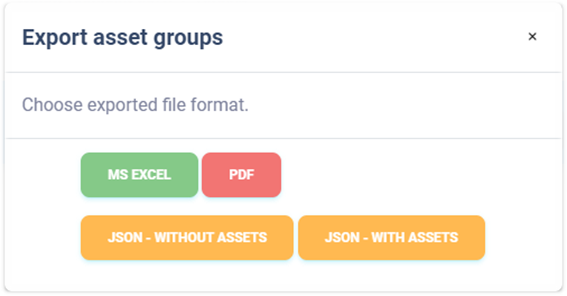
Export to JSON#
Exporting asset groups to JSON format is only available to instance administrators. This type of export can only be used with an Enterprise license. The exported file can serve as a simple backup or can be used to create custom templates for bulk import.
Asset groups can be exported to JSON format in two ways:
Without assets
With assets
Import of assets groups#
Bulk import of asset groups can be performed in the asset management
of the selected client via a modal form that is displayed to the user
after clicking on the Import button.
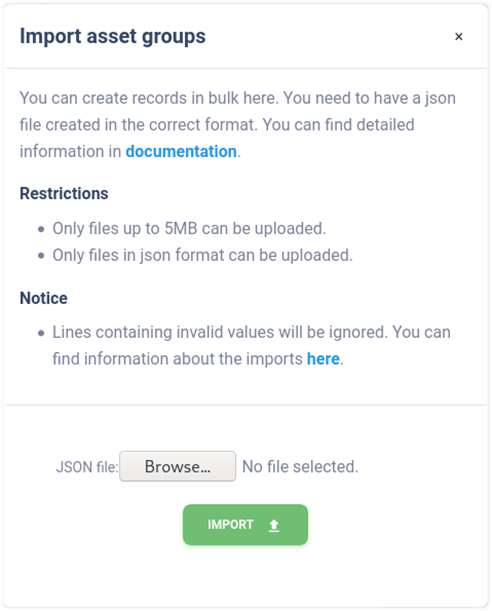
To specify a bulk import of users, a properly created data file must be prepared. Only JSON format files can be imported, and the maximum size is limited to 5MB. Additionally, the uploaded file needs to be properly structured and to contain valid data. We recommend using the ready-made templates at https://riskflow.cz/cs/templates/. The structure of a valid file with two records looks following.
[
{
"title": "Group 1",
"active": true
},
{
"title": "Group 2",
"active": false
}
]
Parameter |
Accepted values |
|---|---|
title |
Alphanumeric string with special symbols |
active |
true / false |
Asset groups can be imported in bulk together with the corresponding assets. For this option, you need to have a file ready for import in the following format.
[
{
"asset_groups": [
{
"title": "Group 1",
"active": true,
"assets": [
{
"identifier": "AS1",
"title": "Asset 1",
"type": "primary",
"short_description": "short description",
"long_description": "detailed description",
"owner": "Pokey Trippy",
"guarantor": "Randy Sleepy",
"availability": "low",
"integrity": "high",
"confidentiality": "critical"
},
{
"identifier": "AS2",
"title": "Asset 2",
"type": "auxiliary",
"short_description": "short description",
"long_description": "detailed description",
"owner": "Squirrely Baggy",
"guarantor": "Cloudy Baggy",
"availability": "critical",
"integrity": "low",
"confidentiality": "low"
}
]
}
]
}
]
Parameter |
Accepted values |
|---|---|
asset_groups |
Array of asset groups |
active |
True / false |
assets |
Array of assets in a particular group |
identifier |
It must be unique within the group. It can be empty. Alphanumeric string special symbols. |
title |
Alphanumeric string with special symbols |
type |
Primary / auxiliary |
short_description |
Alphanumeric string with special symbols |
long_description |
Alphanumeric string with special symbols, can be empty |
owner |
Alphanumeric string with special symbols |
guarantor |
Alphanumeric string with special symbols |
availability |
low / medium / high /critical |
integrity |
low / medium / high /critical |
confidentiality |
low / medium / high /critical |
Templates for bulk import of client’s users#
Risk Flow prepares templates for its clients to create files for bulk import. These templates are publicly available at https://riskflow.cz/templates/. It is allowed to edit and use them for private and commercial purposes.
Verification of the success of the specified import#
Success of the specified bulk imports can be verified in the Log Entries module. This is available at https://INSTANCE-NAME.riskflow.cz/imports/logs or it is possible to get to it through the modal window of bulk import forms
By default, records are sorted by date and time the request was created and contain the following information - status, task name, detailed description of the action result, the user who made the request, name of the uploaded file and its size, and the date and time the request was created.
Tip
Detail of the provided information are described in section Import success verification of this documentation, dedicated to user managamenet.
7.3. Assets#
After selecting an asset group, a listing of the specific assets recorded in that group is displayed. Instance administrators, managers and client users can edit these assets. Analysts and auditors and can only view them. The assets created can be edited and their impact on availability, integrity and confidentiality can be assessed directly in this listing.
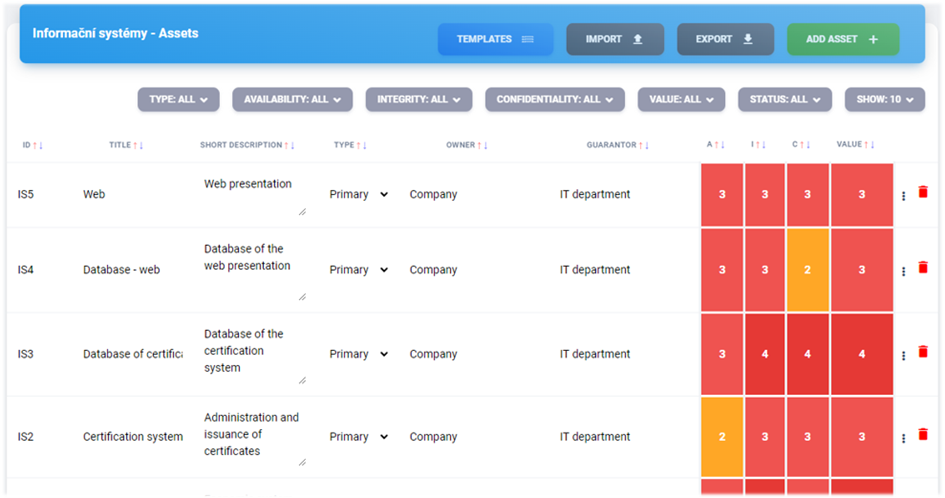
Creating an asset#
The form to add an asset group can be found at https://NAZEV-INSTANCE.riskflow.cz/cs/risks/assets/<ID KLIENTA>/groups/<ID SKUPINY>/assets/create or by clicking on the Add asset button.
Parameter |
Required |
Description |
|---|---|---|
Identification |
Ne |
Asset identification for better orientation. Must be unique within the asset group. |
Title |
Yes |
Asset name |
Asset type |
Yes |
|
Short description |
Yes |
Brief description of the asset. It is displayed in the assets inventory. |
Detailed description |
No |
Detailed description of the asset. It is displayed in the asset detail. |
Asset owner |
Yes |
Identification of the person, organization or department that owns the asset. |
Asset guarantor |
Yes |
The cybersecurity guarantor is a security role responsible for ensuring the development, usage and security of assets. An asset guarantor is also a person who promotes ensuring the confidentiality , availability and integrity of the asset of which it is the custodian. It is appropriate for the guarantor to control the assessment of the asset, as he/she is most familiar with it. |
Edit asset#
Editing the asset is possible after opening the edit form by clicking
the three dots icon. It is also possible to edit assets directly
in the listing of all assets. The availability, integrity and
confidentiality of the asset is also evaluated in this listing. These
three values are then used to calculate the final value of the asset,
which is considered when calculating the value at risk in the
analysis.
View asset details#
Users who do not have the ability to edit assets can view a listing of
assets and their details by clicking on the asset identifier or
description. Users with editing rights can view the full asset detail
in the edit form by clicking the three dots icon.
Availability#
Availability of information means that the information, including the required information systems, must be accessible to any authorised person at any time and usable (functional) to the extent required. If the system fails or is not accessible, the requested information is not available. In certain cases, this can lead to disruptions with far-reaching consequences, for example in process maintenance. The Risk Flow provides the following scale for assessing availability.

Integrity#
The technical term integrity is associated with several requirements:
Unintentional changes to information must be impossible or at least detectable and traceable.
The reliability of data and systems must be guaranteed.
The completeness of the information must be guaranteed.
Risk Flow provides the following scale for assessing integrity.

Confidentiality#
The aim is to protect confidential data from unauthorised access, whether on the grounds of data protection laws or on the grounds of commercial confidentiality, which is covered, for example, by the Trade Secrets Act. Therefore, the confidentiality of information and sensitive data is ensured if only persons who are authorised to access it have an access to it. Access means, for example, reading, editing or even deleting.
The measures taken must therefore ensure that only authorised persons have access to confidential information - unauthorised persons never. This also applies to information on paper, which may be lying unprotected on a desk and inviting to be read, or to the transmission of data that cannot be accessed in the course of processing.
Risk Flow provides the following scale for assessing confidentiality.

Value of the asset#
The asset value is calculated from the specified availability, integrity and confidentiality values and is calculated as the maximum value of these monitored parameters.
Asset value = max(availability, integrity, confidentiality)
Value |
Description |
|---|---|
1 |
The asset is of low value to the organisation. This applies if all its factors are rated low. |
2 |
The asset is of medium value to the organisation. This applies if it is at least one factor from the trio of accessibility, integrity, confidentiality rated medium. |
3 |
The asset is of high value to the organisation. This applies if at least one factor of the triad of availability, integrity, confidentiality is rated high. |
4 |
The asset is of critical value to the organisation. This applies if at least one factor of the triple of availability, integrity, confidentiality is rated critical. |
Delete asset#
You can delete assets by clicking on the trash can icon. When
deleting, it is necessary to confirm the action in the modal window
displayed afterwards. Only assets that are not used in risk analyses
can be deleted.
Export assets#
Export to MS Excel#
Exporting assets to a Microsoft Excel workbook has the following values. The report language is adapted by the currently used application language.
Column name |
Description |
|---|---|
# |
Record number in the export |
ID |
An asset identification |
Short description |
Brief description of the asset |
Asset type |
Primary / Auxiliary |
Owner |
Asset owner |
Guarantor |
Asset guarantor |
Availability |
Low / Medium / High / Critical |
Integrity |
Low / Medium / High / Critical |
Confidentiality |
Low / Medium / High / Critical |
Asset value |
1 / 2 / 3 / 4 |
Created at |
Date the record was created. |
Creation time |
Time the record was created. |
Created by |
Email of user who created the record. |
Modified |
The date when record was last modified. |
Modification time |
The time when record was last modified. |
Modified by |
Email of user who made the last changes. |
Export do PDF#
Exporting assets to PDF format contains an asset inventory similar to the listing in the application. It contains the following information. The report language is adapted by the language currently used in the application.
Column name |
Description |
|---|---|
# |
Record number in the export |
ID |
An asset identification |
Short description |
Brief description of the asset |
Asset type |
Primary / Auxiliary |
Owner |
Asset owner |
Guarantor |
Asset guarantor |
Availability |
Low / Medium / High / Critical |
Integrity |
Low / Medium / High / Critical |
Confidentiality |
Low / Medium / High / Critical |
Asset value |
1 / 2 / 3 / 4 |
Export to JSON#
Exporting assets to JSON format is only available to instance administrators. This type of export can only be used with an Enterprise license. The exported file can serve as a simple backup or can be used to create custom templates for bulk import.
Import of assets#
Bulk import of assets can be performed in the asset management of the
selected client via a modal form that is displayed to the user after
clicking on the Import button.
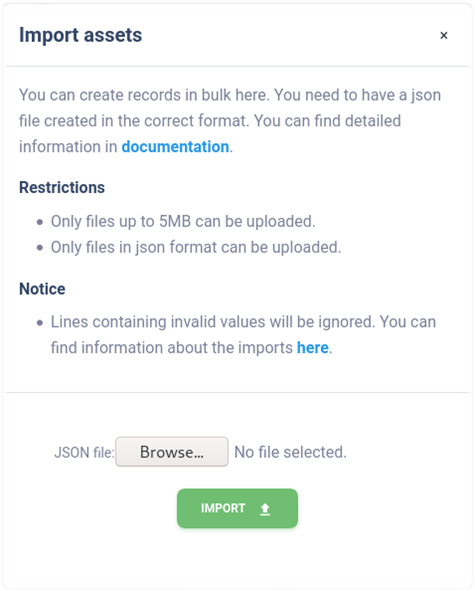
To specify a bulk import of assets, a properly created data file must be prepared. You can only import files in JSON format, the maximum size of which is limited to 5MB. It is also necessary that the uploaded file has the correct structure and contains valid data. We recommend using the templates available at https://riskflow.cz/templates/. The structure of a valid single record file is following.
[
{
"identifier": "A1",
"title": "Asset 1",
"type": "primary",
"short_description": "short description",
"long_description": "detailed description",
"owner": "Pokey Trippy",
"guarantor": "Randy Sleepy",
"availability": "low",
"integrity": "high",
"confidentiality": "critical"
}
]
Parameter |
Accepted values |
|---|---|
identifier |
Alphanumeric string with special symbols |
title |
Alphanumeric string with special symbols |
type |
Primary / auxiliary |
short_description |
Alphanumeric string with special symbols |
long_description |
Alphanumeric string with special symbols |
owner |
Alphanumeric string with special symbols |
guarantor |
Alphanumeric string with special symbols |
availability |
low / medium / high / critical |
integrity |
low / medium / high / critical |
confidentiality |
low / medium / high / critical |
Templates for bulk import of assets#
Risk Flow prepares templates for its clients to create files for bulk import. These templates are publicly available at https://riskflow.cz/templates/. It is allowed to edit and use them for private and commercial purposes.
It is always recommended to verify the integrity of downloaded files. This verification ensures that the file has not been corrupted or altered during the download. To verify the success of the download, we use an MD5 hash that can be found in the download table.
Tip
A tutorial on how to perform this verification can be found in section Templates for bulk user import
Verification of the success of the specified import#
Success of the specified bulk imports can be verified in the Log
Entries module. This is available at
https://INSTANCE-NAME.riskflow.cz/imports/logs or it is possible to
get to it through the modal window of bulk import forms.
By default, records are sorted by date and time the request was created and contain the following information - status, task name, detailed description of the action result, the user who made the request, name of the uploaded file and its size, and the date and time the request was created.
Tip
Detail of the provided information are described in section Import success verification of this documentation, dedicated to user managamenet.
