9. Risk analyses#
Supporting the execution of risk analysis is the most important feature of the Risk Flow platform. This module describes in detail the used methodology.
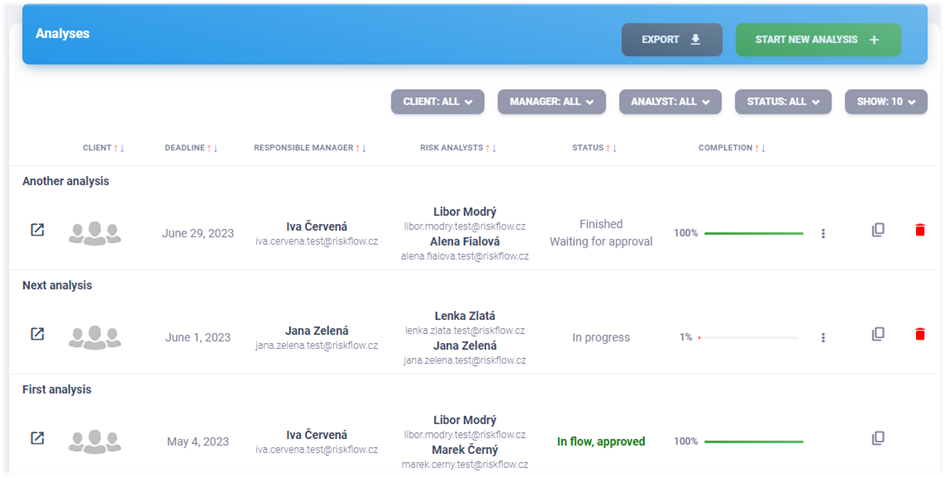
9.1. View a list of risk analyses#
After navigating to the Analyses module, the user is presented with
a list of all risk analyses to which they have rights to access. The
distribution of permissions in this case is as follows:
Admin |
Has rights to see and edit all available unfinished analyses. |
|---|---|
Manager |
He has rights to see and edit the risk analyses, that he has created and to which he has been assigned by the administrator. A user with the manager role also has all the privileges of an analyst. |
Analyst |
Has the rights to perform the risk analysis, to which he is assigned. Does not have rights to edit risk analysis parameters but can edit analysis lines and request manager approval. Can add comments. |
Client |
Has the rights to view and comment on the risk analyses that have been created for his Company. |
Auditor |
Has read-only access to all sections, can add comments. |
9.2. Create risk analysis#
It is possible to create a risk analysis on the Risk Flow platform by
clicking on the button Start a new analysis or by opening
https://NAZEV-INSTANCE.riskflow.cz/cs/analysis/create.
Parameter |
Required |
Description |
|---|---|---|
Client |
Yes |
Selecting client for whom the risk analysis will be performed. |
Analysis title |
No |
Title of the risk analysis. It is used for better orientation in the system. |
Responsible |
Yes |
Only users with the |
Risk analysts |
No |
Users with the role |
Deadline |
Yes |
Setting a deadline to resolve. Cannot be set in the past or at today’s date. |
After successful creation of the risk analysis, the assigned analysts and manager are notified by email. The user who triggered the action does not receive an informational email, i.e., if the manager creates the analysis, he does not receive an informational email about the assignment to the risk analysis. In this way, Risk Flow tries to minimize the number of informational emails.
9.3. Edit risk analysis#
Editing the risk analysis is possible in the update form, which the user
can open in the list analyses via the three dots icon or in the risk
analysis detail via the Edit button.
9.4. Copying risk analysis#
A user with editing rights to a specific risk analysis can create copies
of it. When copying a risk analysis, the same parameters must be set as
in time of creating a new risk analysis. In this process, all rows of
the risk analysis are duplicated. This feature is very useful when
revising previously completed risk analyses. Copying a risk analysis can
be done via the copy icon in the list of all available risk analyses
or in the details of a specific risk analysis. The responsible manager
and analysts are notified by email of the assignment to the analysis.
9.5. Delete risk analysis#
You can delete a risk analysis in the list of available risk analyses or in the details of a specific analysis. An authorized user can delete those risk analyses that are not part of any approval processes.
9.6. Export risk analyses#
Export of analyses is possible in the appropriate module by clicking on
the Export button and selecting the export type.
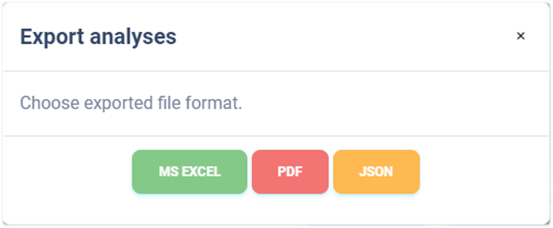
Export to MS Excel#
Exporting a list of risk analyses to a Microsoft Excel workbook has the following values. The language of the report is adapted by the currently used language of the application.
Column name |
Description |
|---|---|
# |
Record number in the export |
Client |
Client name |
Deadline |
Deadline date |
Responsible manager |
A user with the role of |
Analysts |
List of users with the role |
Stav |
|
Completion |
Analysis progress expressed in %. |
Created at |
Date the record was created. |
Creation time |
Time the record was created. |
Created by |
Email of user who created the record. |
Modified |
The date when record was last modified. |
Modification time |
The time when record was last modified. |
Modified by |
Email of user who made the last changes. |
Export to PDF#
Exporting the analysis list to PDF format contains a list similar to the list in the application. It includes the following information. The language of the report is adapted by the currently used language of the application.
Column name |
Description |
|---|---|
# |
Record number in the export |
Client |
Client name |
Deadline |
Deadline date |
Responsible manager |
A user with the role of “Risk Manager” who is responsible for completing the risk analysis. |
Analysts |
List of users with the role “Risk analysts” who are/ were involved in performing risk analysis. |
Stav |
|
Progress |
Analysis progress expressed in %. |
Export to JSON#
Exporting assets to JSON format is available only to instance administrators. This type of export can only be used with an Enterprise license. The exported file can serve as a simple backup or can be used to import into third-party applications.
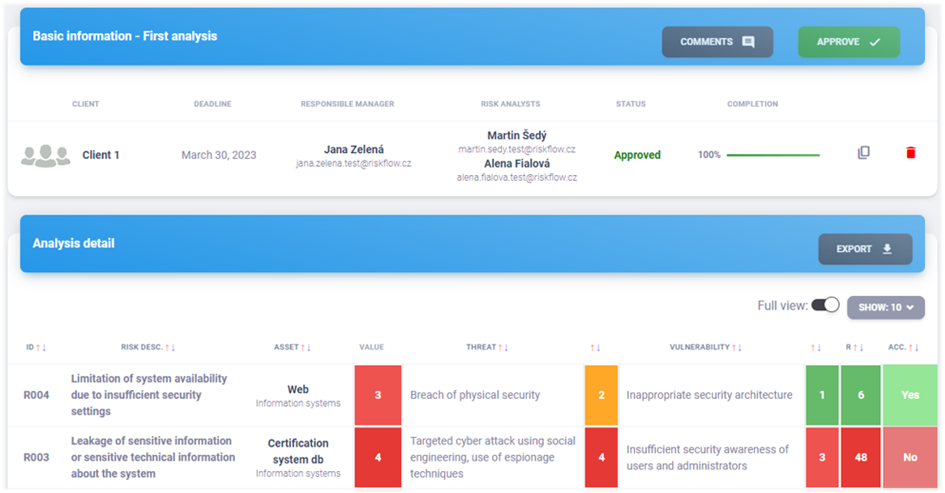
9.7. Risk analysis detail#
Authorized persons may consult the risk analyses available to them. The administrator or responsible persons can add and edit risk analysis rows. Users with edit permissions can edit not yet approved risk analyses directly in the risk analysis detail, just as asset management works.
Adding risk analysis row
The form for adding risk analysis row can be found at
https://INSTANCE-NAME.riskflow.cz/en/analysis/<ANALYSIS ID>/row/create or by clicking on the Add Row button.
In this form, you can take advantage of the Risk Flow catalog, from which specific texts describing risks, threats and vulnerabilities can be drawn. Searching the catalog works after entering at least three characters and its use is demonstrated in the following image.
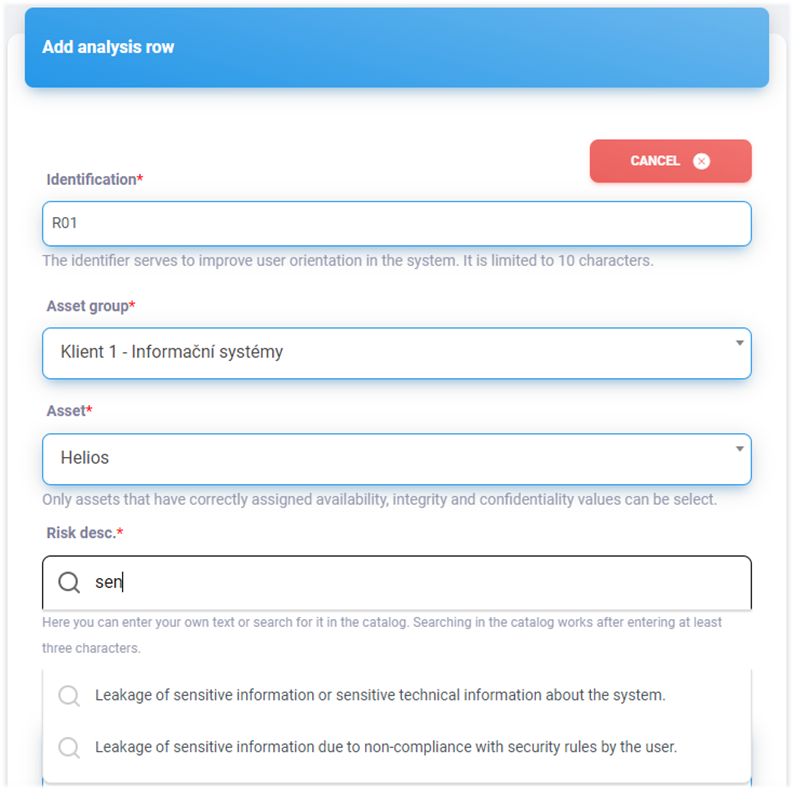
Use of the risk catalog is possible in this form for the following fields – Risk description, Threat, Vulnerability.
Managers and analysts can add to the risk catalog by leaving the Add to risk catalog box checked. The catalog can be used by all managers
and analysts for all risk analyses, and therefore texts specific to
the client being processed should not be added to the catalog. Only
the instance administrator has rights to edit the catalog.
Parameter |
Required |
Description |
|---|---|---|
Identification |
Ne |
The identifier is used to improve user orientation in the system. It is limited to 10 characters. |
Asset group |
Yes |
To select an asset, you must first select an asset group. This list is filtered to show only the asset groups of the respective client. |
Asset |
Yes |
Selection of the asset to which the recorded risk applies. Can only be selected after selecting the asset group. This list is filtered to show only the assets of the selected group. In risk analysis it is only possible to use assets, which are fully evaluated in terms of availability, integrity and confidentiality. |
Risk description |
Yes |
Brief description of the risk recorded – for example, leakage of sensitive information, infiltration of the system or application, unavailability of services, etc. |
Detailed description of the risk |
No |
Detailed description of the recorded risk. |
Threat |
Yes |
A threat exploits the vulnerability of an asset and can cause damage or disruption to it. Threats can be, for example, natural disasters, accidents, social phenomena, economic phenomena or individual behavior. It is always necessary to consider the threats relevant to the asset and the context of the organization. |
Detailed threat description |
No |
Detailed description of the threat. |
Vulnerability |
Yes |
A vulnerability is a weakness (lack) of an asset or a weakness (lack) of a security measure that can be exploited by one or more threats. |
Detailed description of vulnerability |
No |
Detailed description of the vulnerability. |
Measure |
No |
A method of protecting an asset to mitigate the magnitude of risk. |
Edit analysis row#
An authorized user can edit risk analysis rows directly in the risk
analysis detail or in the detail of the specific row after opening the
respective form by clicking on the three dots icon. It is possible
to use the advantages of the Risk Flow catalog, as when adding an
analysis line.
Delete analysis row#
An authorized user can delete rows of a risk analysis not yet approved
directly in the detail of the risk analysis of a specific line after
opening the relevant form by clicking on the trash bin icon and
then confirming in the modal window.
Evaluation#
Only assets that are fully rated for availability, integrity and confidentiality in asset management can be used in risk analysis. To calculate the risk value of an analysis line, three values are required - asset value, threat value, vulnerability value. Since the asset value is calculated by creating and rating the asset in asset management, the threat and vulnerability values remain to be defined in this step.
The value at risk is calculated as follows:
RISK = ASSET x THREAT x VULNERABILITY
Risk calculation and acceptance#
When all the necessary data is defined for an analysis row, Risk Flow calculates the risk value. This is an integer falling in one of the following ranges.

Risk may or may not be accepted. It is based on the final risk assessment and the scale is defined as follows.

Exporting risk analysis details#
Export of risk analysis details is possible by clicking on the Export button and then selecting the type exports.
Export to MS Excel#
Exporting the risk analysis detail to a Microsoft Excel workbook has the following values. The report language is adapted by the currently used application language.
Column name |
Description |
|---|---|
# |
Record number in the export. |
ID |
The identifier is used to improve user orientation in the system. |
Risk desc. |
Brief description of the risk recorded - for example, leakage of sensitive information, infiltration of the system or application, unavailability of services, etc. |
Detailed description of the risk |
Detailed description of the recorded risk. |
Asset |
Selection of the asset, to which the recorded risk applies. Can only be chosen after selecting the asset group. This list is filtered to show only the assets of the selected group. Only assets that are fully rated for availability, integrity and confidentiality in asset management can be used in risk analysis. In risk analysis it is only possible to use assets, which are fully evaluated in terms of availability, integrity and confidentiality. |
Asset value |
1 / 2 / 3 / 4 |
Threat |
A threat exploits the vulnerability of an asset and can cause damage or disruption to it. Threats can be, for example, natural disasters, accidents, social phenomena, economic phenomena or individual behavior. It is always necessary to consider other threats relevant to the asset and the context of the organization. |
Detailed threat description |
Detailed threat description. |
Value |
Low / Medium / High / Critical |
Vulnerability |
A vulnerability is a weakness (lack) of an asset or a weakness (lack) of a security measure that can be exploited by one or more threats. |
Detailed description of the vulnerability |
Detailed description of the vulnerability. |
Value |
Low / Medium / High / Critical |
Risk |
Calculated risk value, a number from the interval <1, 64>. |
Accepted |
Yes / No |
Measure |
A method of protecting an asset to mitigate the magnitude of risk. |
Created at |
Date the record was created. |
Creation time |
Time the record was created. |
Created by |
Email of user who created the record. |
Modified |
The date the record was last modified. |
Modification time |
The time the record was last modified. |
Modified by |
Email of user who made last changes. |
Export to PDF#
Exporting the risk analysis details to PDF format contains a list similar to the listing in the application. It includes the following information. The language of the report is adapted by the currently used language of the application.
Column name |
Description |
|---|---|
ID |
The identifier is used to improve user orientation in the system. |
Risk desc. |
Brief description of the risk recorded - for example, leakage of sensitive information, infiltration of the system or application, unavailability of services, etc. |
Asset |
Selection of the asset, to which the recorded risk applies. Can only be selected after selecting the asset group. This list is filtered to show only the assets of the selected group. Only assets that are fully rated for availability, integrity and confidentiality in asset management can be used in risk analysis. In risk analysis it is only possible to use assets, which are fully evaluated in terms of availability, integrity and confidentiality. |
Asset value |
1 / 2 / 3 / 4 |
Threat |
A threat exploits the vulnerability of an asset and can cause damage or disruption to it. Threats can be, for example, natural disasters, accidents, social phenomena, economic phenomena or individual behaviour. It is always necessary to consider other threats relevant to the asset and the context of the organization. |
Value |
Low / Medium / High / Critical |
Vulnerability |
A vulnerability is a weakness (lack) of an asset or a weakness (lack) of a security measure that can be exploited by one or more threats. |
Value |
Low / Medium / High / Critical |
Risk |
Calculated risk value, a number from the interval <1, 64>. |
Accepted |
Yes / No |
Measure |
A method of protecting an asset to mitigate the magnitude of risk. |
Export to JSON#
Exporting risk analysis rows to JSON format is only available to instance administrators. This type of export can only be used in the Enterprise license. The exported file can serve as a simple backup or can be used to import into third-party applications.
9.8. Risk analysis approval#
Once all risk analysis lines have been completely evaluated and the risk analysis progress parameter shows a value of 100%, the analysis can proceed to approval.
Request for approval of completed risk analysis#
A user with the role of manager or analyst can submit a request for approval of an analysis. The responsible manager is notified of the request by email and prompted to take action.
Approval or return for refinement#
Approval of implementation is made by the responsible manager of the specific analysis. Once an analysis is approved, it is locked for editing and can be further used in approval flows. Until the analysis is approved by the responsible manager, it can be further edited. As long as the analysis is not part of an approval flow, the responsible manager can withdraw his approval and return the analysis to the analysts for refinement.
9.9. Comments#
View comments#
Authorized users can add comments to all risk analyses. All comments
can be viewed by clicking on the Comments button, which opens a
page with a list of existing comments and a form to add a new one.
Adding comment#
You can add a comment after filling in the appropriate field for
entering the text of the comment and submitting it by clicking the
Add comment button.
Internal and public comments#
Users can add internal and public comments. Internal comments are not displayed to the clients for whom the risk analysis is processed. Administrators, managers, analysts and auditors can see all registered comments and attachments.
Attachments#
You can add attachments to each comment. To select multiple attachments, hold down the CTRL key and left-click to select multiple files to upload, or select all files to upload and drag them with the mouse into the file upload box.


